Cybersecurity Awareness Training

What is Cybersecurity Awareness?
“awareness training is a recognized practice for educating employees about cyber security”
TOPICS INCLUDE:
- Employees and contractor responsibilities in handling sensitive information, including review of employee nondisclosure agreements.
- The nature of sensitive material and physical assets users may come into contacts with, such as intellectual property, personally identifiable information, and sensitive financial data.
- Proper methods of protecting sensitive information, including password policy and use of multi-factor authentication.
- How users can recognize and report Malware, Phishing, Social Engineering, etc.
- Consequences of failure to properly protect the information, include the potential loss of employment, economic consequences to the company, damage to individuals whose personally identifiable information is divulged, and possible criminal penalties.
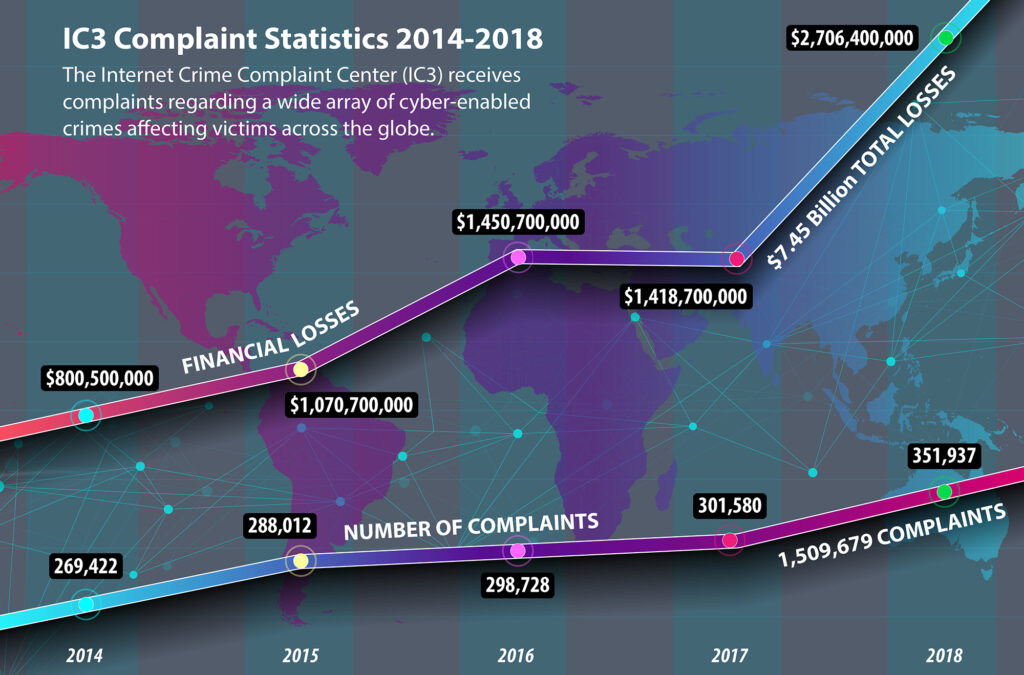
- Every 11 seconds, a Ransomware incident occurs
- Over 800,000 people fall victim to cyber-attacks
- Cybercrime costs 2.9 million every minute for organizations.
OUR TRAINING PROCESS
C18 offers group awareness training and more personalized service to increase self-awareness and bring about a desirable transformation in their corporate and personal lives. We also recommend annual refreshers, at a bare minimum.
INITIAL MEETING
Understanding your environment and building a plan specifically designed for your organization.
PLAN & TRAIN
Our next step would be to supply training to your organization based on employee schedules.
LESSONS LEARNED
Touch base on the results of the training across your organization to identify further training gaps.

PHISHING ATTACKS
The practice of sending fraudulent communications that appear to come from a reputable source.
SOCIAL ENGINEERING ATTACKS
Art of manipulating someone to divulge sensitive or confidential information via phone or txt.
RANSOMWARE ATTACKS
Software that is designed to damage, encrypt, steal data, extort companies and destroy systems.
POLICIES AND PROCEDURES
Need to make sure that your organization has the proper policies and procedures in place.
HOW CRIMINALS GET YOU!
Companies and organizations in the United States, as well as multiple foreign governments, were harmed by theft of intellectual property, trade secrets, and other highly valuable information by Advanced Persistent Threat (APT). By establishing initial access, the APT exploits user and administrator credentials to enable lateral movement within the network and locate high-value assets to exfiltrate data. To reduce risk, network defense procedures should be implemented and comply with best practices. These guidelines can facilitate managing the risk and mitigating the threat.
- By stealing compromised credentials, an attacker can obtain victim identity information.
- Criminals create new email accounts and hack existing ones to conduct social engineering attacks.
- Spear phishing emails are sent containing malware and malicious attachments.
- Malware is used to exploit various common vulnerabilities and exposures by exploiting software vulnerabilities in
applications.
Referenced from cisa.gov